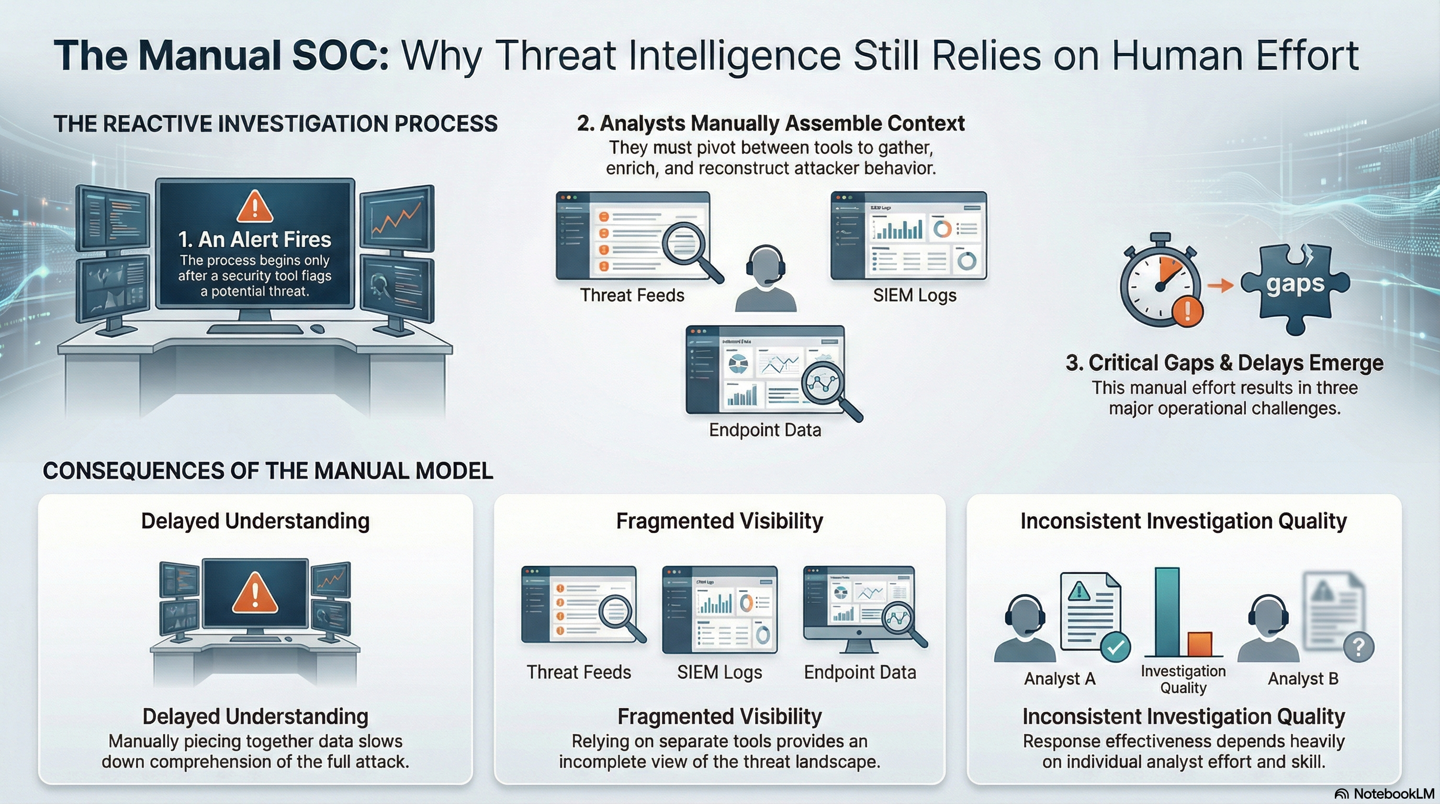
Manual threat intelligence remains the default operating model in many SOCs. Analysts are still expected to gather, enrich, and interpret context by hand, pivoting between tools, stitching together partial views, and reconstructing attacker behaviour only after alerts fire.
The cost of this approach is not limited to slower investigations. It shows up as cognitive exhaustion, inconsistent intelligence quality, and SOC teams that stay busy without ever feeling ahead of the attacker.
Most teams are not failing to detect threats. They are failing to understand them quickly enough.
The Problem: Manual Threat Intelligence Has Become the Default Operating Model
Figure 1: Manual context gathering slows analysis and increases operational risk1.png
Despite heavy investment in SIEM, EDR, XDR, cloud security, identity platforms, and threat intelligence feeds, many SOCs still depend on analysts to manually collect, enrich, and interpret alerts.
This reliance on human-driven context assembly carries a measurable operational cost.
Enterprise Management Associates (EMA) reports that security teams must navigate between 10 and 22 different security management interfaces [Source] to “get the job done.” In practice, this means that a single investigation often requires an analyst to pivot across five to ten tools, including the SIEM, endpoint detection platform, identity provider, cloud console, and external enrichment services.
This fragmentation is not accidental. It is structural.
In parallel, Microsoft has stated that a single alert can require up to 30 minutes of manual triage [Source]. That time is typically spent separating signal from noise, validating indicators, checking user and asset context, and determining whether the alert warrants deeper investigation.
Before analysis even begins, time has already been consumed assembling basic understanding.
As telemetry volumes continue to grow, this operating model becomes increasingly fragile. New tools often expand the number of interfaces analysts must touch, rather than reducing the manual effort required to interpret alerts.
This creates several systemic issues across SOC workflows:
- Manual enrichment and interpretation remain the analyst’s responsibility
- Investigations span multiple disconnected systems by default
- Intelligence quality varies by analyst experience, time pressure, and shift coverage
- Knowledge is captured in tickets or personal memory rather than shared context
- Enrichment begins only after alerts fire, when investigations are already underway
- Visibility remains focused on individual indicators instead of attacker behaviour
The result is a persistent paradox. SOCs generate enormous volumes of telemetry, yet decision-making remains slow and inconsistent. The challenge is not a lack of data. It is the reliance on manual processes to transform that data into understanding.
The Enrichment Tax: When Context Comes at the Cost of Time
In many SOCs, enrichment is treated as a routine investigative step. Its cumulative cost is rarely tracked.
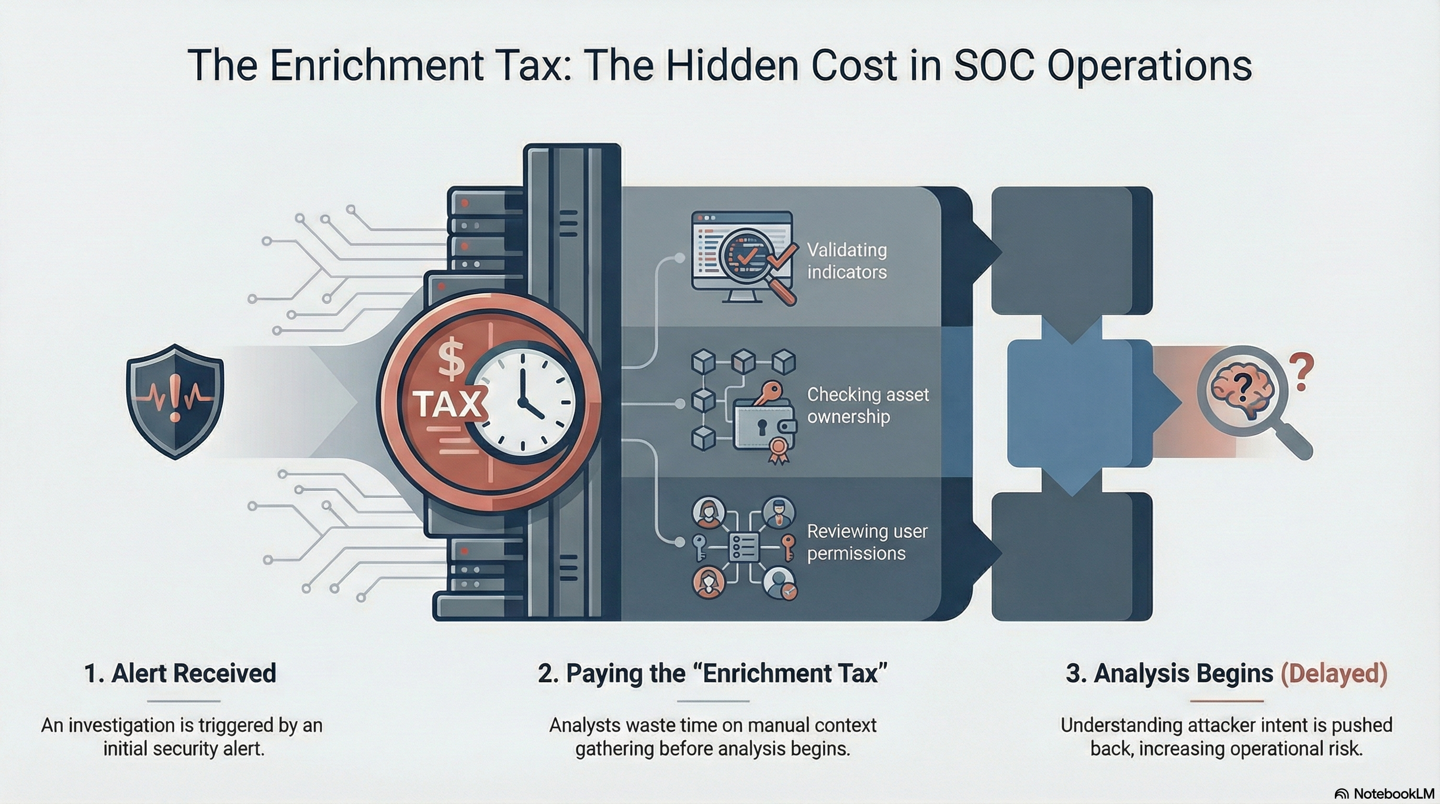
Microsoft’s data highlights the scale of this issue. If up to 30 minutes are required per alert for manual triage, much of that time is not spent analysing attacker intent. It is spent gathering context. Analysts check asset ownership, validate user permissions, and review historical activity, and cross-reference indicators across tools.
This is the Enrichment Tax.
Figure 2 : Manual context gathering delays analysis and increases risk2.png
That thirty-minute window represents time lost before meaningful analysis even starts. During this period:
- Analysts manually copy indicators between systems
- Context is gathered through repetitive lookups
- Confidence is built incrementally rather than systematically
- This enrichment-heavy workflow introduces several operational risks:
- Large portions of analyst time are consumed by low-value manual work
- Investigation depth varies based on individual effort and familiarity with tools
- Analysts prioritize what is fastest to access rather than what is most relevant
- Investigation timelines expand even when threats themselves are not more complex
The cost of this tax is paid in delayed decisions, prolonged attacker dwell time, and rising cognitive load across the SOC. Teams invest heavily in tooling, yet analysts must work harder simply to reach baseline understanding.
The Pivot Penalty: Context Switching Across a Siloed SOC Stack
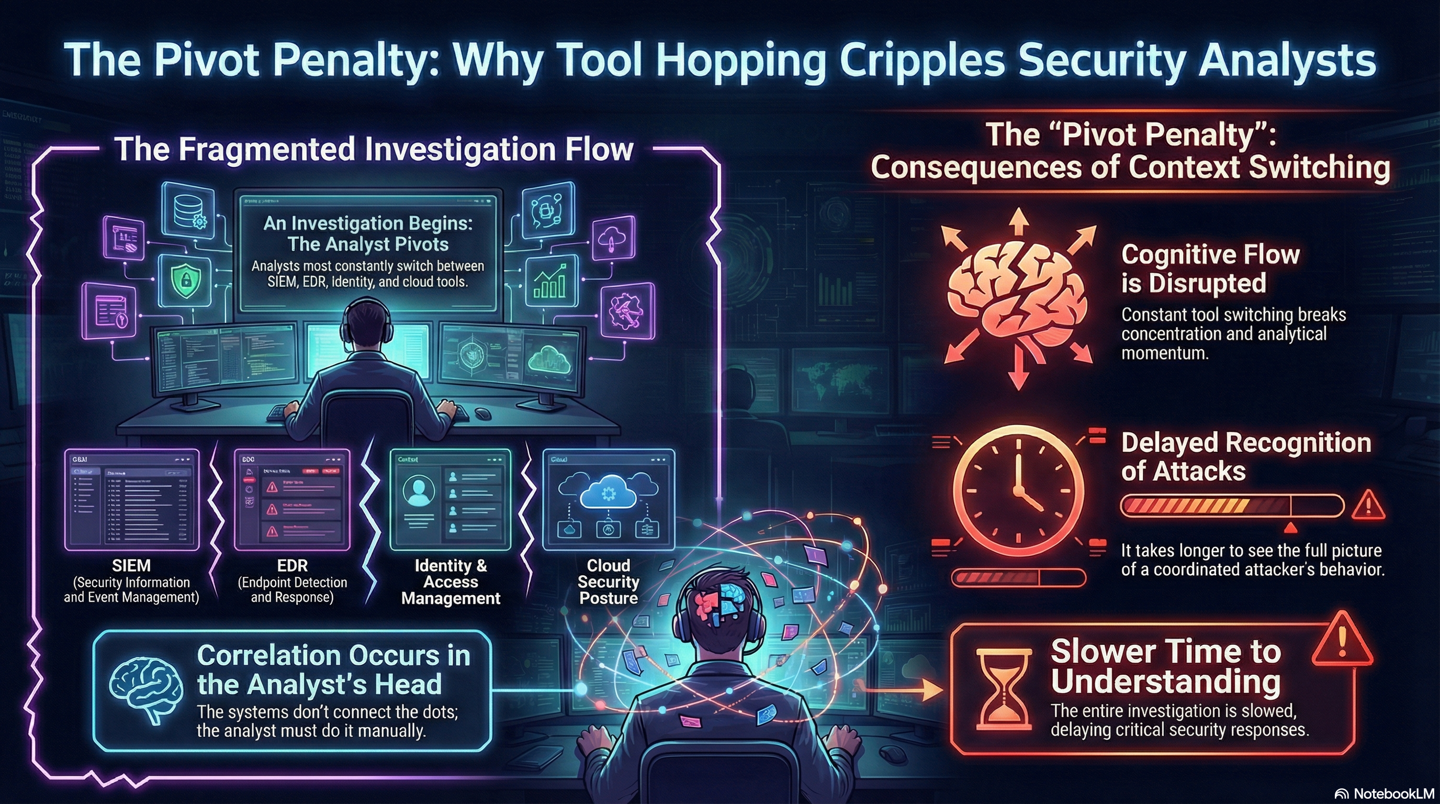
Figure 3: Tool switching slows correlation and understanding.3.png
EMA’s finding that security teams operate across 10 to 22 interfaces explains why investigations feel fragmented by default.
When analysts must pivot between five to ten tools for a single case, correlation does not occur in the system. It occurs in the analyst’s head.
This constant context switching introduces the Pivot Penalty.
The cost is not just elapsed time. It is the loss of cognitive flow.
Each screen change forces analysts to reorient, recall prior findings, and mentally stitch timelines together. Over the course of a shift, this repeated interruption degrades judgment and slows recognition of coordinated attacker behaviour.
This pivot-heavy workflow produces predictable outcomes:
- Visibility remains partial in every system
- Correlation is manual and error-prone
- MITRE ATT&CK mappings remain static and disconnected
- Attack paths are reconstructed late in the investigation
- Analyst fatigue accumulates long before alerts are resolved
As SOC stacks grow more complex, the Pivot Penalty compounds. Understanding arrives late not because analysts lack skill, but because the operating model fragments their attention.
Human Bottlenecks in Threat Validation and MITRE Mapping
In many SOCs, the speed and quality of threat validation are constrained by analyst availability and experience. During periods of high alert volume or reduced staffing, validation slows, queues grow, and decisions are deferred. The limitation is not detection capability, but the reliance on human-only decision points embedded throughout the workflow.
This reliance creates several operational challenges:
- Threat validation is limited by analyst capacity rather than system intelligence
- Manual MITRE ATT&CK mapping introduces inconsistency across cases and teams
- Low-confidence alerts are deprioritized, even when they represent early attack stages
- Intelligence quality varies across shifts, depending on who is on duty
- Human-only validation and escalation points restrict scale and throughput
The operational impact is cumulative. SOCs detect activity at scale, but validation and understanding progress at human speed. As manual decision points multiply, investigations' slow and consistent TTP visibility becomes increasingly difficult to maintain.
The Mental Shift: From Manual Intelligence to AI-Augmented SOC Operations
Reducing the hidden cost of manual threat intelligence requires a fundamental change in how intelligence is produced.
ThreatLens is designed to address the thirty-minute enrichment tax directly.
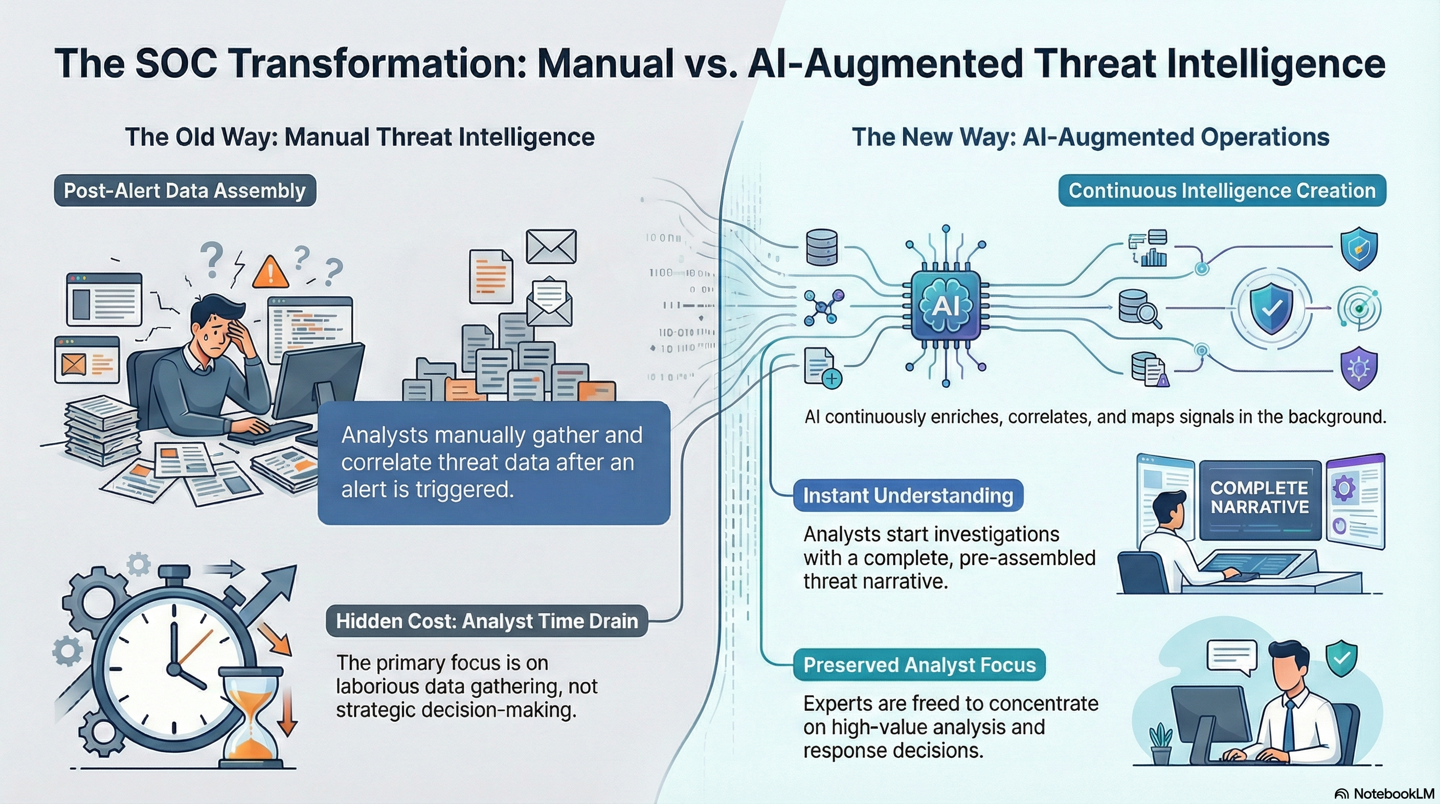
Instead of forcing analysts to manually pivot across tools and assemble context after alerts fire, ThreatLens performs continuous intelligence creation in the background. Signals from identity, endpoint, cloud, and network telemetry are enriched, correlated, and mapped as they are generated.
By the time an analyst opens a ticket, the manual triage has already occurred.
The system has built the narrative. Who the user is. Which assets are involved? How the activity maps to known techniques. Where it fits within a broader behavioural pattern.
This operating model:
- Eliminates repeated tool pivoting
- Preserves analyst cognitive focus
- Creates consistent intelligence across shifts
- Enables earlier recognition of coordinated attacker behaviour
Success is no longer measured by alert throughput. It is measured by speed of understanding.
Figure 4 : Continuous intelligence enables faster understanding and better decisions.4.png
Where This Leads Next
Manual threat intelligence keeps SOCs reactive. Context is assembled after alerts fire, understanding is delayed by manual enrichment, and insight depends heavily on analyst effort rather than shared intelligence. The challenge is not detection, but the reliance on static indicators and human-driven interpretation to explain attacker behaviour.
If indicators alone cannot provide meaning, threat intelligence must move beyond them.
This shift, from indicators to intelligence built on behaviour, techniques, and context, is continued in Blog 3: From Indicators to Intelligence: Why IOCs Alone Are No Longer Enough.