Why Modern SOCs Are Drowning in Alerts, but Still Missing Real Threats
It’s 9:17 a.m. in the SOC. An analyst opens the alert queue and is met with hundreds of new alerts, most categorized as Low or Informational. Routine detections dominate the list, masking a lateral movement event unfolding quietly across multiple systems. On its own, it lacks the severity to demand attention. By the time it is recognized, the opportunity for early containment has already passed.
Modern Security Operations Centres generate more alerts than ever, yet meaningful threat understanding remains elusive. SIEM, EDR, and XDR platforms produce constant activity that creates the appearance of strong security posture, while analysts spend their time triaging alerts and rebuilding context across fragmented tools. As activity increases, attacker behaviour becomes harder to distinguish. This post examines the structural and operational reasons modern SOCs remain overwhelmed while still missing real threats.
img1.png
The Illusion of Coverage: Why Alert Volume Is Mistaken for Security
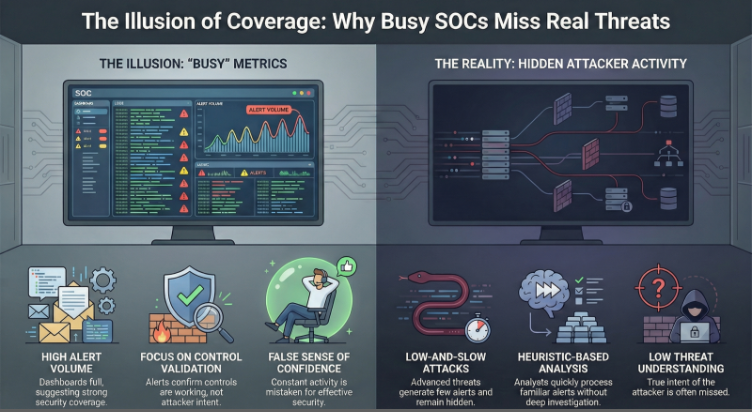
Modern SOC dashboards are designed to signal activity and reassurance. Alerts fire consistently, queues stay full, and metrics suggest a healthy security posture. In reality, this activity often reflects coverage rather than understanding. Many detections exist to confirm that controls are firing, not to explain attacker intent or guide investigation. As a result, SOCs accumulate alerts that show something triggered, but rarely clarify what it means or what should happen next.
Over time, this environment conditions analyst behaviour. When alerts become predictable, analysts learn to trust dashboard indicators instead of questioning signal quality. Familiar detections are processed quickly, often without deeper scrutiny, because efficiency is rewarded over exploration. This leads to:
- Faster closure of known alert patterns
- Reduced willingness to investigate subtle deviations
- Growing reliance on heuristics instead of analysis
Meanwhile, low-and-slow attacker activity often persists quietly, generating fewer alerts and remaining less visible in volume-driven metrics.
The result is a false sense of confidence. SOCs appear busy, controls appear effective, and reports show steady detection, yet meaningful security outcomes lag behind. When coverage is defined by alert volume rather than threat understanding, activity becomes a misleading proxy for security
Alert Fatigue Degrades Analytical Judgment before It Causes Burnout

img2.png
Alert fatigue is often framed as a staffing or burnout issue, but its earliest and most damaging effects are cognitive. Sustained alert pressure forces analysts into constant triage, where rapid decisions are made with limited context and little time for hypothesis-driven investigation. Frequent context switching across tools further disrupts analytical flow, reducing the ability to build and maintain a coherent understanding of attacker behaviour.
Over time, this operating environment produces several compounding effects:
- Alerts are evaluated independently rather than as part of attacker behaviour
- Heuristics and pattern recognition replace structured investigation
- Subtle deviations are missed as attention is drawn to familiar patterns
The most critical outcome is not exhaustion, but missed threats. Telemetry is present, but attention is fragmented. Low-confidence signals that indicate slow or subtle attacker movement fail to stand out amid alert volume. Threats are overlooked not because data is unavailable, but because sustained cognitive overload limits the ability to interpret it effectively.
Fragmented Telemetry Obscures Attacker Behaviour
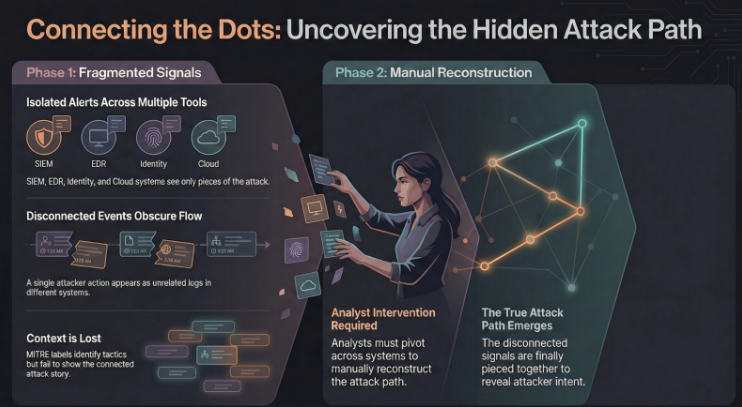
Modern SOCs collect large volumes of telemetry across SIEM, EDR, and XDR platforms, but each tool captures only a partial view of activity. Network, endpoint, identity, and cloud signals are recorded independently, causing the same attacker action to appear as unrelated events. Telemetry enrichment and MITRE-mapped detections add labels and additional data, but without strong correlation, they increase volume without explaining how activity connects across time or systems. As a result, analysts see isolated techniques rather than a coherent view of attacker progression or intent.
In practice, this fragmentation creates several challenges:
- The same attacker behaviour is represented differently across tools
- Related signals remain disconnected despite existing in the environment
- MITRE-mapped detections provide classification without showing attack flow
- Attack path reconstruction happens manually and often late
- Understanding attacker intent becomes dependent on individual analyst effort
To make sense of this fragmentation, analysts manually reconstruct attack paths by pivoting across tools, timelines, and case notes. This process is slow, inconsistent, and highly dependent on experience, often occurring after alerts have already been triaged or closed. Ultimately, SOCs are not constrained by a lack of telemetry, but by the loss of meaning when signals remain disconnected, making real-time understanding of attacker behaviour difficult.
img3.png
SOC Operations Optimize for Triage, Not Understanding
Most SOCs are structured around fast alert handling rather than sustained threat comprehension. Success is measured by alerts closed, response times met, and queues reduced. These metrics are easy to report, but they say little about whether attacker intent was understood or disrupted.
Escalation workflows reinforce speed over context, especially during high-volume periods. Investigations often begin after evidence has already been scattered across systems, reducing the likelihood of identifying coordinated or low-and-slow attacks.
This model produces predictable outcomes: Investigations start late, after context has fragmented Individual techniques are visible, but attack lifecycle connections are missed Risk prioritization is driven by volume rather than behaviour or intent
Over time, SOCs become highly efficient at managing alerts while adversaries adapt by operating below thresholds and spreading activity across time and systems. The gap widens between operational efficiency and real security effectiveness.
Where This Leaves the Modern SOC
If alerts are firing, controls are working, and telemetry is abundant, why does threat understanding still feel manual? Why does intelligence depend so heavily on individual effort, intuition, and after-the-fact reconstruction?
If alerts are not the real problem, what is missing between detection and understanding?
That question leads directly to the next conversation: why threat intelligence in modern SOCs still feels stubbornly manual, and what it would take to change that.
Continued in Blog 2: The Hidden Cost of Manual Threat Intelligence in Security Operations
