Modern Security Operations Centers are flooded with data. Logs, alerts, telemetry, and threat feeds arrive nonstop, all promising visibility into risk. Yet despite this volume, many SOC teams still struggle to answer a basic question:
What is the attacker actually doing right now?
For years, threat intelligence has been built around indicators of compromise such as IP addresses, file hashes, and domains.
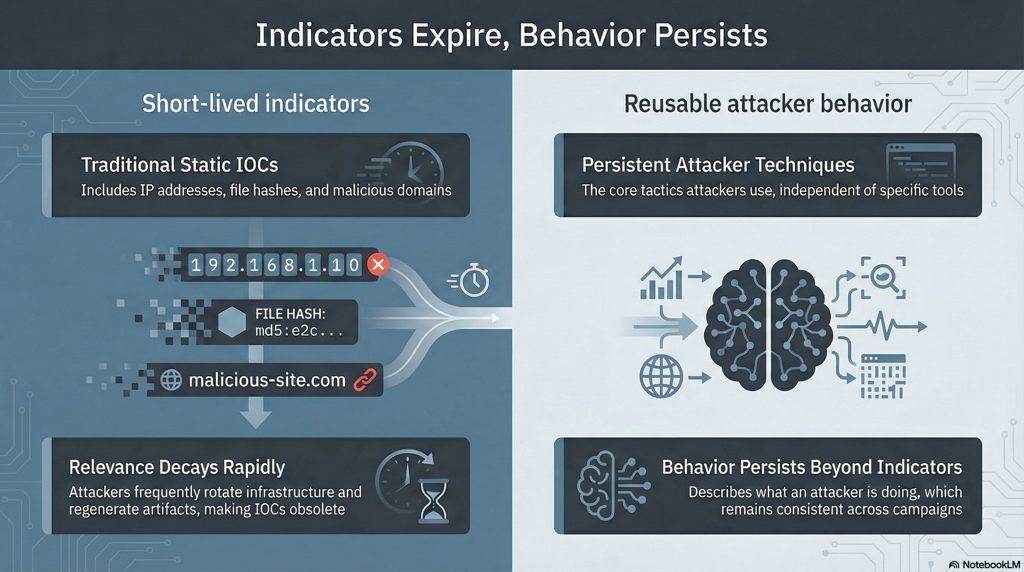
Figure 1 : Indicators expire. Behavior persists.1.png
These indicators still matter, but on their own, they no longer provide the clarity needed to defend modern environments.
The shift from indicators to intelligence is not just technical. It is a fundamental change in how security teams detect, investigate, and respond to threats.
Problem: Static Indicators Create Alert Fatigue
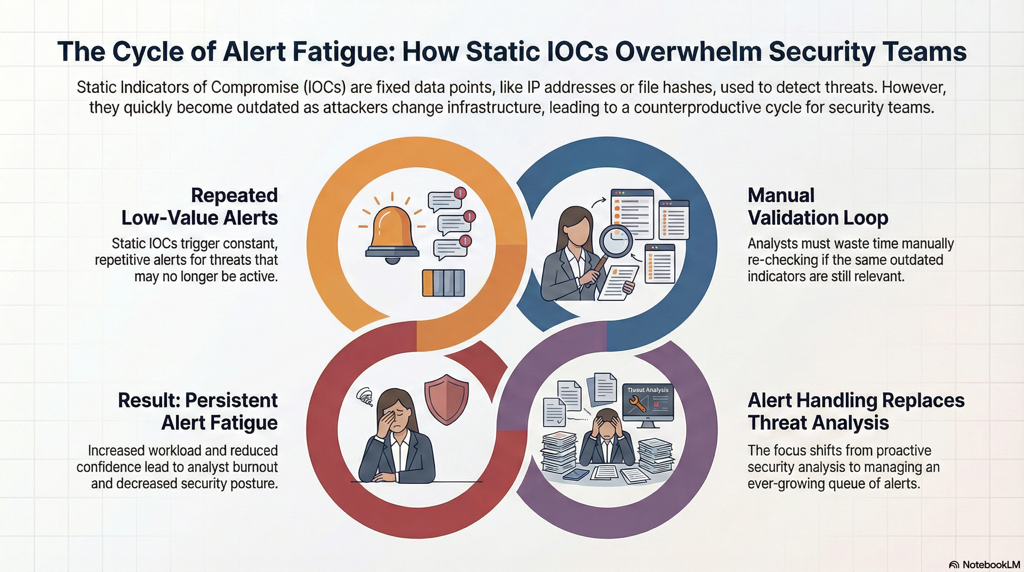
Figure 2 : Alert volume grows while understanding declines.2.png
Static IOCs were designed for a threat landscape where attackers reused infrastructure and malware for long periods. That world no longer exists.
Today’s attackers rotate IP addresses, regenerate artefacts, abuse legitimate cloud services, and blend malicious activity into normal operational patterns. As a result, IOC-based detections degrade rapidly. By the time an alert is investigated, the indicator itself is often no longer meaningful.
This creates a familiar SOC problem:
- Alerts fire repeatedly based on low-value or outdated indicators
- Analysts must manually validate whether an IOC is still meaningful
- The same checks are performed again and again across different tools
Over time, SOCs shift into alert handling mode rather than threat analysis. Workload increases, confidence erodes, and alert fatigue becomes the default operating condition.
Indicators do not fail because they are wrong. They fail because they are incomplete.
Impact: Noise Hides Real Attacker Behavior
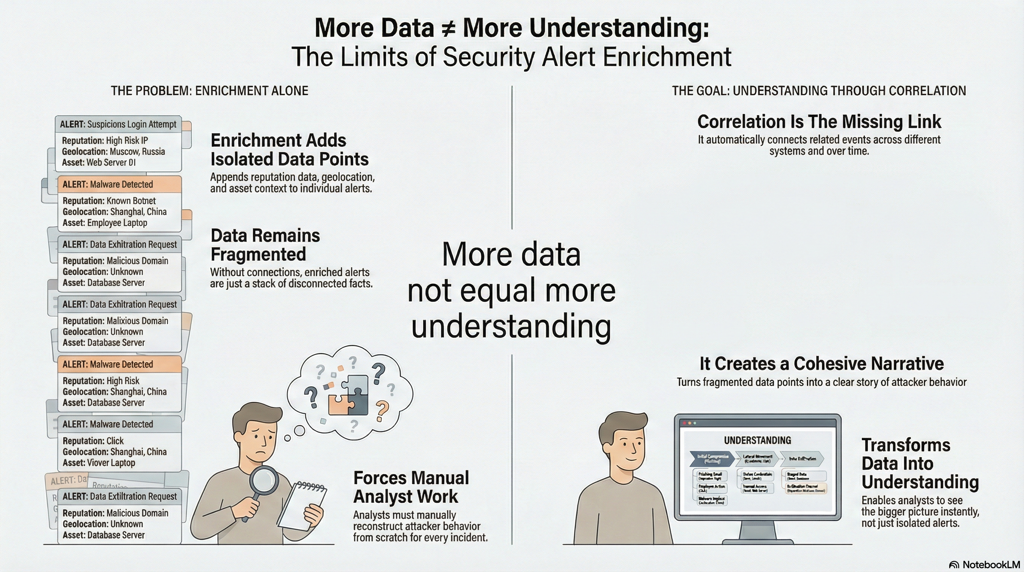
To compensate for weak indicators, SOCs enrich alerts with more data. Reputation scores, geolocation, asset context, historical activity, and user information are layered onto each signal.
This creates the appearance of progress. But enrichment alone does not produce understanding.
An analyst with one hundred enriched logs is still just a person with one hundred logs.
Figure 3 : More data without correlation becomes noise. Without correlation, enrichment becomes noise. Analysts are left answering tactical questions:3.png
- Is this IP malicious?
- Has this hash been seen before?
- Does this domain appear in a feed?
What they are not consistently answering are the questions that actually matter:
- Which technique is unfolding?
- How far has the attacker progressed?
- What is the likely next step?
Understanding does not come from adding more attributes to isolated events. It comes from recognizing patterns across time, systems, and behavior.
A Better Mental Model for Intelligence
To move beyond indicators, SOCs need a different way to think about intelligence. Not as artefacts to be checked, but as a progression to be understood.
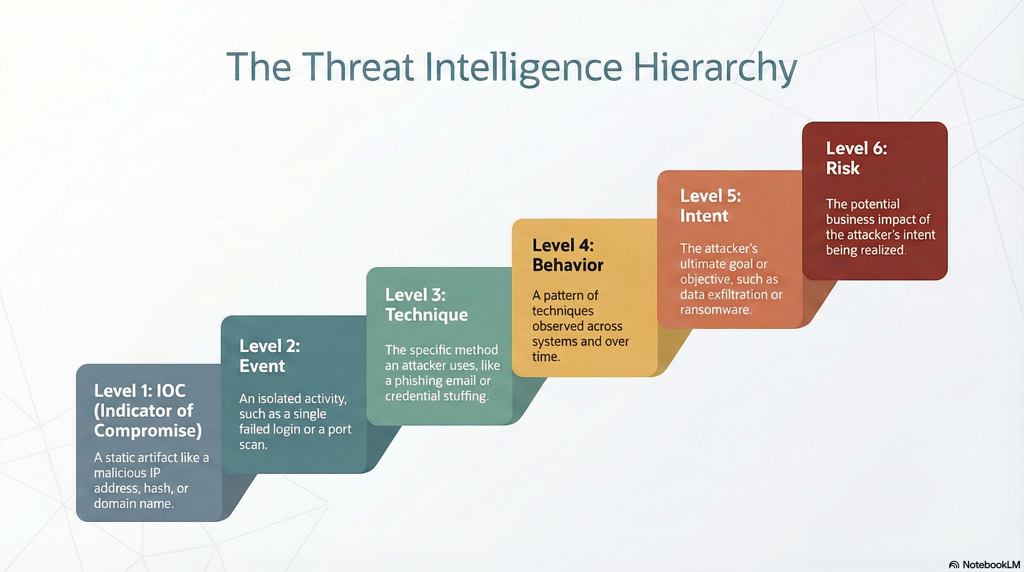
A mature intelligence model follows a clear hierarchy:
- IOC: The static marker. A hash, domain, or IP address.
- Event: An occurrence. A login, a process execution, a file access.
- Technique: The method. Credential access, lateral movement, persistence.
- Behavior: The pattern. How techniques chain together across systems and time.
- Intent: The purpose. Why the attacker is acting, and what they are trying to achieve.
- Risk: The impact. What this behavior means to the business.
Figure 4 : Intelligence begins where indicators end.4.png
Most SOC workflows stop at the first or second level. They detect IOCs and events, enrich them, and move on. But intelligence only emerges higher in the hierarchy, where behavior, intent, and risk become visible.
This is the difference between knowing that something happened and understanding what is happening.
Why Behavior Reveals What Indicators Cannot
Modern attacks rarely trigger a single high-confidence indicator. Instead, they unfold as a series of small, explainable actions. A login here. A token is used there. An access attempt that looks routine in isolation.
Viewed individually, none of these events justify escalation. Viewed together, they form an attack path.
This is why indicator-driven workflows struggle with slow, multi-stage attacks. The telemetry exists, but without behavioral correlation, the narrative remains invisible. By the time impact is detected, the opportunity for early intervention has passed.
Understanding attacker behavior requires systems that can reason across events, map techniques over time, and surface intent before damage occurs.
From Indicators to Intelligence in Practice
The purpose of an intelligence-driven SOC is not to eliminate indicators. It is to put them in their proper place.
Indicators become inputs, not conclusions.
In an intelligence-first model, activity is continuously observed and correlated across identity, endpoint, cloud, and network domains. Events are interpreted through the lens of known techniques. Behaviors are assembled into narratives. Intent is inferred. Risk is assessed in business terms.
When an analyst engages, they are not confronted with a list of alerts. They are presented with an evolving story.
This is the difference between chasing alerts and understanding attacks.
Indicators still play a role in modern security operations, but they are no longer sufficient on their own. Intelligence emerges only when events are connected, techniques are understood, and behavior is interpreted in context. Without this shift, SOCs remain reactive, overwhelmed by data yet slow to understand what truly matters.
Moving from indicators to intelligence is not just a technical upgrade. It is a change in how analysts work, how decisions are made, and how risk is understood.
If intelligence must be behavioral, contextual, and continuous, the next question becomes practical: what does this actually look like inside the SOC?
That question is explored next in Blog 4: What Does an AI-Augmented SOC Analyst Actually Look Like?